Cloud Security
CloudPassage Delivers Elastic Security in a Dynamic Cloud

Cloud computing has dramatically changed the way organizations approach security. CloudPassage co-founder and CEO Carson Sweet explains how the company’s Halo product can deliver scalable, elastic security in public and hybrid cloud environments.
To learn more about CloudPassage visit their website or review their product profile.
How has cloud computing changed the way companies approach security?
Dramatically is the right way to think about it. The big change here is that things are outside of what traditionally has been a very contained environment. For 20 some-odd years now we’ve relied on firewalls and perimeter technology to protect everything, and as these perimeters and walls have started to dissolve people have started to adopt cloud computing. They’ve put data outside their firewall with SaaS providers. They’ve put servers outside of their walls with Infrastructure-as-a-Service providers like EC2 and Rackspace. The risk posture changes pretty dramatically. They lose a lot of control. For example if you put servers in an external environment with an Infrastructure-as-a-Service provider, you lose control of the hardware, the IP address, and the topology, and that makes it a lot harder to secure things. So just the technical nature of cloud computing makes security very different.
How was CloudPassage founded and what is its mission?
So the mission is to allow companies to leverage cloud computing safely in multiple models.
We started about two years ago. I’ve been in security for about 20 years and was very deeply immersed in the virtualization security world, which was a new set of issues in the late ’90s. When cloud computing was first starting out, we recognized that there was going to be a significant set of technical challenges with securing these public Infrastructures-as-a-Service environments and very large-scale private cloud environments as well. So I’d already seen some of this in previous work with large financial institutions and government agencies.
When we started to see the public side take off we began talking to the companies that were the earliest adopters of cloud computing and did indeed find out that there were some significant technical problems to be met.
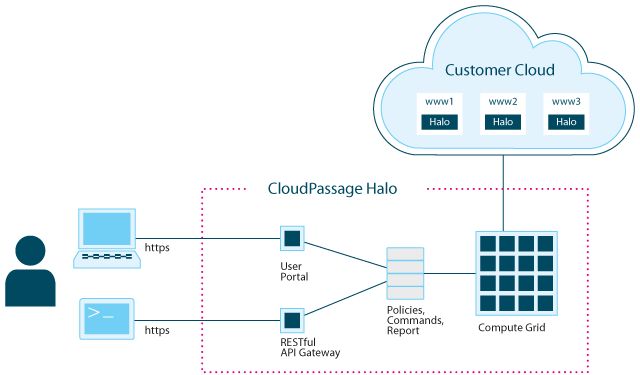
When we talked to the large companies about cloud computing again two years ago, they really wanted to use it. The business units in particular wanted the flexibility, the cost granularity, and the scalability of cloud, but their compliance teams and security teams simply wouldn’t allow it. We saw a lot of shadow IT start to emerge, where business units would set up cloud operations on their own.
All of these things drove us to look at how we can address that fundamental problem of how to let businesses use the cloud safely, whether they’re a large company that wants to move something to the cloud or a start-up company who has grown to the point where security becomes an important issue for them. Those are really the underlying market drivers and technical drivers that got the company off the ground in the first place.
What are some of the primary threats that Halo protects your clients against?
We focus on the virtual machine itself—the cloud server. When you read articles about someone who’s compromised a vulnerability in Microsoft’s RDP protocol or someone who’s exploited a vulnerability in the configuration of a server, or a database password, it’s things like this. We focus on the underlying infrastructure. When you build an application in the cloud it’s very important that the servers it runs on—the foundational component that everything else operates on top of—are actually very secure.
The application security is obviously very important as well. We focus on that by making sure the platforms that your applications run on a little higher up in the stack are also configured in a secure way. There’s a very good report by Verizon Business that comes out every year. Typically one of these reports will indicate that 90% plus of the data compromises that occur in a given year are due to misconfigurations, bad software, things like that. Very simple things that need to be taken care of. Although it sounds like it should be easy, the challenge of doing this is the scale—when you have thousands of servers, hundreds of servers and something that needs to be automated very deeply. And that’s what we do. We automate the process by taking care of all the owner’s details and making sure there’s no chink in the armor if you will.
What types of companies stand to benefit from your services?
The companies that we work with the most are SaaS providers. Those are the companies building on cloud like crazy because Infrastructures-as-a-Service gives them the opportunity to scale their business over time.
We see a lot of large established software companies moving to cloud because they need to be able to compete with the start-ups. You look at the very large providers that have traditional on-premise software. SaaS is a big deal for them, they like to use Infrastructure-as-a-Service for that because it makes them more agile and more nimble.
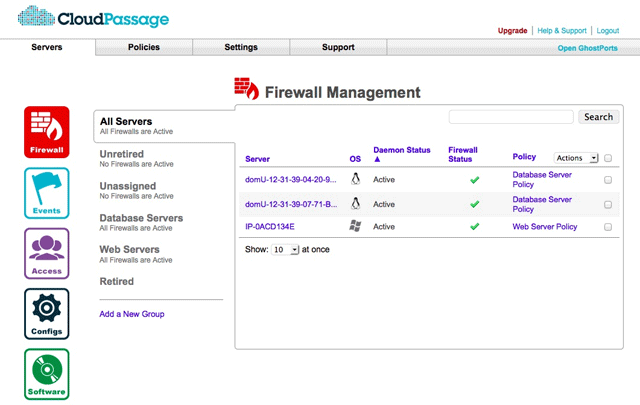
There are a number of sectors that are heavy users of cloud and Infrastructure-as-a-Service today, including financial services, genomics, and biotech. Over time we think it’s going to be a model that most companies adopt. There will be resources that are both in private and public environments and there will be abstraction layers that lay on top of that. It’s already happening with a lot of big early adopters today, and it’s getting to the point where some of these more advanced companies don’t even think about where their resources are. It’s so automated and the orchestration layer abstracts away the actual infrastructure to the point where the applications just exist in a true cloud. Some of that resides in the data centers and some of that resides in one cloud provider and some may reside in another.
So we focus on that orchestration layer for security. Making sure that the security is consistent no matter where your resources happen to live.
What does CloudPassage do differently and how do you stand out from the industry noise?
So the big difference in how we deliver security is that we’re built for the cloud explicitly, we’re not an existing technology that someone’s trying to jam into a cloud model. We actually secure the cloud itself. You see a lot of security solutions that are delivered from the cloud, but that doesn’t actually secure the cloud itself. The fact that we are built for cloud specifically means that we can deal with things like the elasticity that exists in the cloud. That’s a technical characteristic that means you can take ten servers and replicate those into a hundred or a thousand servers in a matter of minutes, literally. That’s never been available before, and traditional security products don’t deal with that very well, if at all.
Another example is the lack of hardware and network control that you have in a public cloud environment. We deal with all those issues, and make it so that the customer doesn’t have to worry about them any longer. This is a huge need and we’re the only company that does this.
We also follow the cloud procurement model very closely. Most traditional security products are licensed by the seat or by the CPU or something along those lines. When you purchase cloud computing, and even for large companies that are doing advanced private cloud computing, they look at costs by the hour. So if you go to EC2 you’re actually paying for your server by the hour.
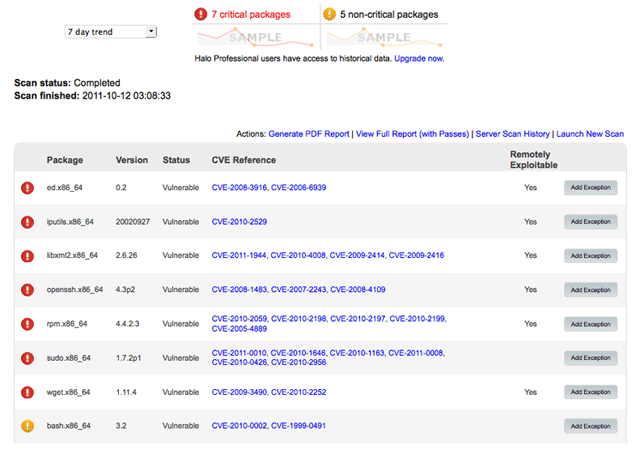
You purchase security from CloudPassage by the hour as well, which is a unique model, but it’s an important model because that’s how you buy cloud servers, and security for the cloud servers being a function of cost of cloud servers, you also need to be able to procure the security by the hour as well. It doesn’t make any sense to buy five hours of a server’s time and pay for a full month’s worth of security or a whole year’s worth of security.
Where do you see cloud security heading in the next five years and how do you see CloudPassage fitting into that landscape?
So in the sector that we live in it’s really about abstraction of resources. We think that security is going to follow along with new infrastructure models. We think that most organizations will have an abstracted cloud environment, which means they will have private cloud environments built on Eucalyptus for example, or VMware or CloudStack. And they’ll have public resources. We typically hear the phrase ‘lease the spikes.’ The idea there is that you have a baseline environment. If you know you need, let’s say, 5,000 servers all the time, you run those privately, and upon seasonal demand or week-to-week demand or whatever your particular business model drives, you need to burst up. You have spikes of utilization that require an extra 500 servers during the month of July for example. Then you use public resources to do that. Today that process is not quite completely abstracted. Over time we think that’ll become more and more abstracted so it becomes very seamless.
So when the Internet first became a commercial issue, everyone had leased lines. Everyone had private network connectivity between their data centers, and over time the Internet evolved and the security technologies and deployment and orchestration technologies evolved to the point where really the Internet became an integral part of the overall communications infrastructure for a company, and that’s the norm now.
And we think the same thing will happen over time with infrastructure, and security’s got to come along for the ride there as well. So really cloud security is going to be about dealing with the abstraction of infrastructure, taking that concept with the Internet up a level. That’s really what we are chasing and what we’re focused on bringing to the table.
What are some of the challenges that you face and how do you overcome them?
The biggest challenge that we faced was how to make all of this work in the cloud and across multiple cloud environments. We overcame that through engineering—there’s really no other way to put it.
From a go-to-market perspective, the biggest challenge that we face is education. We’re on an early part of the adoption program for cloud computing. The companies that have been around for a while—like Zynga and Netflix—they get it. They really understand how cloud security is different, so they immediately engage and see our value proposition.
When you look at companies that are just starting out in the cloud there’s a shift that has to take place from thinking about a perimeter model and a data center environment, where you can get away with a lot more because you’ve got those walls and moats, to thinking more about each individual server as something that has to be self-defending. Instead of having soldiers in plain clothes behind a wall, now you’ve got to have little suits of armor for everybody, and they have to be self-protecting. And thinking in that way is quite different.
The other big challenge is people flounder around to see what standard they should look for. There’s a very important organization called the Cloud Security Alliance. We’re part of the Cloud Security Alliance, and we work very closely with them to provide guidance to people about cloud security, but it’s still very early days.
So much of Internet security was undefined 20 years ago, and cloud security standards and requirements are still relatively undefined today, and that’s a big challenge for us because it’s an education process that we take our customers through, which takes time. But as with any early market, that education will come over time, things will solidify and the best models will emerge. We think we’ve got one of those best models.
Who are some other interesting players in cloud security right now?
![]() In terms of cloud security, the other company that we find particularly interesting is CloudFlare. CloudFlare is a hybrid company that does Web application security and performance together, which is a very interesting model. What we find interesting about them is that they’re also focused on trying to consumerize security and make it very easy to deal with, which is one of the things that we focus on. They focus on a different layer in the stack than we do. They really focus on the actual Web application flow itself, where we’re looking at the underlying components that all of that runs on top of.
In terms of cloud security, the other company that we find particularly interesting is CloudFlare. CloudFlare is a hybrid company that does Web application security and performance together, which is a very interesting model. What we find interesting about them is that they’re also focused on trying to consumerize security and make it very easy to deal with, which is one of the things that we focus on. They focus on a different layer in the stack than we do. They really focus on the actual Web application flow itself, where we’re looking at the underlying components that all of that runs on top of.
But the idea is that infrastructure now is consumerized. You don’t need to call IT and wait for five weeks to get a server. You can just go to Amazon, Rackspace, Datapipe, or any of these companies and get a server in a matter of minutes, and then you can make that server go to ten servers in a few more minutes, and then a hundred go to 1,000. So that consumerization of infrastructure means that a number of things under the hood also need to be consumerized, or made very easy and fast. Security is one of those, and CloudFlare is one of the only other security companies we’ve seen that on any scale has really made that possible, which to us is very compelling and it’s one of the enabling factors in cloud.
![]() One of the other companies that is indirectly in the security space that we find very interesting and work with quite a bit is RightScale. RightScale does that abstraction layer I’m talking about across multiple clouds, but they do it for server management generally, not security. We partner with them very closely to add the security layer on top of that larger orchestration layer. That orchestration is very key to enabling cloud, so we find them to be an interesting company as a key cloud enabler.
One of the other companies that is indirectly in the security space that we find very interesting and work with quite a bit is RightScale. RightScale does that abstraction layer I’m talking about across multiple clouds, but they do it for server management generally, not security. We partner with them very closely to add the security layer on top of that larger orchestration layer. That orchestration is very key to enabling cloud, so we find them to be an interesting company as a key cloud enabler.
![]() AppDirect is another very interesting company. We do quite a bit of work with AppDirect on the marketplace side, and part of this consumerization trend in cloud is the way that software gets distributed. It’s not shrink-wrapped and shipped anymore. AppDirect is one of the first companies who has really gotten a good strong hold on a new distribution model—the idea of a marketplace that’s integrated with cloud providers directly.
AppDirect is another very interesting company. We do quite a bit of work with AppDirect on the marketplace side, and part of this consumerization trend in cloud is the way that software gets distributed. It’s not shrink-wrapped and shipped anymore. AppDirect is one of the first companies who has really gotten a good strong hold on a new distribution model—the idea of a marketplace that’s integrated with cloud providers directly.
So if you’re using Rackspace for example, that cloud provider user wants to get their security and their performance management and all the other stuff that they need for their cloud servers from that one provider, and that means there’s a new marketplace opportunity there, and AppDirect has jumped on that new channel model for cloud-delivered software.
![]() And another that we find to be very interesting–again, looking at all the different sectors that orbit around cloud in general—is Zuora. They’re a billing company and one of the few companies who can handle this utility model that we use to do hourly billing. The sales models, the billing models, and the deal structures are so different from what you traditionally see, it does require something that’s specifically built for it and Zuora is one of the really interesting companies that we work closely with that does that new billing model for cloud.
And another that we find to be very interesting–again, looking at all the different sectors that orbit around cloud in general—is Zuora. They’re a billing company and one of the few companies who can handle this utility model that we use to do hourly billing. The sales models, the billing models, and the deal structures are so different from what you traditionally see, it does require something that’s specifically built for it and Zuora is one of the really interesting companies that we work closely with that does that new billing model for cloud.
What are the most exciting things happening with CloudPassage right now?
Probably the most exciting things happening right now are the partnerships. We’re obviously on a great velocity track and we love to see that, but we’re seeing a lot of cloud providers really stepping up and recognizing that security is something their customers want to have imbedded directly in their environment.
We recently announced a partnership with Rackspace, where we’re directly integrated with their environment. People will be able to get security straight through their Rackspace account, which is a very exciting thing for us and for Rackspace.
We’re also working in early stages with companies like Datapipe, another cloud provider. There are a few others that are too early to talk about, but we have about six of these cloud providers that are actively working to imbed our technology directly into their cloud environments, which is incredibly exciting for us, because becoming part of the stack is a very deeply stable place to be.
Looking for the right cloud security software for your business? Be sure to download our free Top 10 Enterprise Cloud Backup Solutions report and compare the top cloud security vendors by pricing and key features. For more information on cloud backup, endpoint security or mobile device management, go to our IT management resource center page, where we have compiled the best product reviews and blog posts on IT software.






